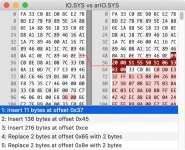
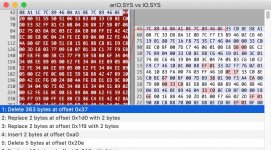
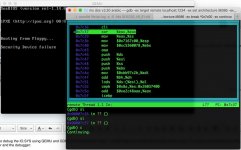
The boot sector has the same 3.30 string as a generic MS-DOS but, yes, there are sub-version numbers that are different to make sure the binaries fail.
Re: "font rom" or whatever, according to the sketchy docs that are out there (and also visible in the display selection part of the installer, which you can run after booting from plain DOS) the major requirement for running this version of DOS, other than the security device, is you need to have display hardware with software definable fonts. That means plain MDA/Hercules and CGA are out, but in addition to EGA/VGA it supported a range of other oddball code-page-capable cards.
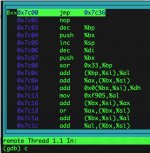
There might be someone smart enough on this forum to disassemble the boot code and figure out a way to neuter the security device requirement, but that person isn't me. How hard it might be may well depend on whether there is just the one check in the DOS initialization code or if checks against that device are peppered all over the code.