Hugo Holden
Veteran Member
I thought I would start a new thread on this and a summary of what transpires.
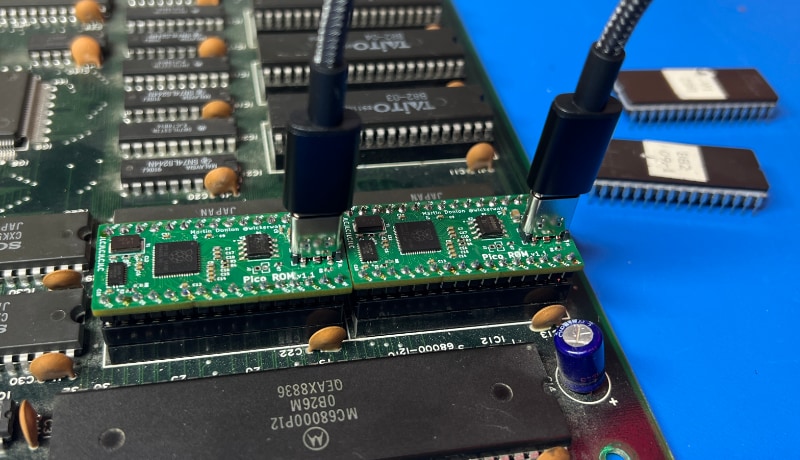
This has been built to help solve a problem that has been bothering me since the 1980's, how to replicate this IC for one of my vintage Conrac VDU's. The original ROM file is not available. I want to extract the file from the original IC in the VDU.
I have just finished the Programming pcb for this CPU-Eprom IC. I thought I would do a professional job on this project, no breadboard wires to cause troubles and foul up the experiments. I followed Motorola's pcb design fairly closely but added some headers to connect to the data lines and some jumpers to disable the clock and use an external slow clock. And disable the programming voltage too. It took me a while to acquire all of the parts. It works by loading a program from a ROM like a 2532, into the CPU's-ROM and then verifying the file. This firmware is in the CPU.
The idea, initially at least, is to get used to programming some of these blanked CPU IC's with a known array of bytes.
Once that is accomplished (which is not the hard part I suspect) then comes the tricky part:
It was suggested by Daver2 that the CPU probably contains an undocumented protocol (firmware program) where it will output the internal ROM byte file. It is a matter of trying to tell it to do it, by manipulating some pin voltages. I will know if I have succeeded because I will know the byte array in the trial IC.
I don't know yet if this will work, but I am hoping it will. I will report the findings on this thread later.
This has been built to help solve a problem that has been bothering me since the 1980's, how to replicate this IC for one of my vintage Conrac VDU's. The original ROM file is not available. I want to extract the file from the original IC in the VDU.
I have just finished the Programming pcb for this CPU-Eprom IC. I thought I would do a professional job on this project, no breadboard wires to cause troubles and foul up the experiments. I followed Motorola's pcb design fairly closely but added some headers to connect to the data lines and some jumpers to disable the clock and use an external slow clock. And disable the programming voltage too. It took me a while to acquire all of the parts. It works by loading a program from a ROM like a 2532, into the CPU's-ROM and then verifying the file. This firmware is in the CPU.
The idea, initially at least, is to get used to programming some of these blanked CPU IC's with a known array of bytes.
Once that is accomplished (which is not the hard part I suspect) then comes the tricky part:
It was suggested by Daver2 that the CPU probably contains an undocumented protocol (firmware program) where it will output the internal ROM byte file. It is a matter of trying to tell it to do it, by manipulating some pin voltages. I will know if I have succeeded because I will know the byte array in the trial IC.
I don't know yet if this will work, but I am hoping it will. I will report the findings on this thread later.