voidstar78
Veteran Member
I understand there were various Models of the IBM System/360, so that alone makes it hard to do a general disassembly of S360 binary.
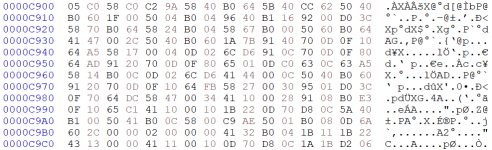
But suppose the binary below (starting at 0x200) is some kind of S360 machine code. I don't think it is the earliest Model 20, don't think it is a Model 40. I do think some floating pointing code might be in there.
The arrangement is below is HxD on a Wintel platform. My understanding is the S360 was big-endian -- but I'm not exactly sure what that means. Meaning, do I reverse the entire byte? Or do I just swap bytes within a word?
For example, the sequence below starts with "50 C0 D1 DC" (I understand not all S360 opcodes were 32-bit, but just examining the first "word" as an exercise)
How would that get interpreted by a S360?
Or maybe no adjustment is needed, if this binary was extracted in the same order the machine interprets it as? Under that premise, then are any of those even valid opcodes?
50 --> don't think this is a valid S360 opcode
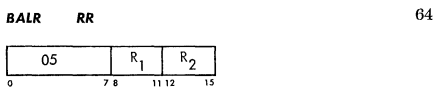
05 --> Branch and Link (BALR)
C0 --> don't think this is a valid S360 opcode
CD --> don't think this is a valid S360 opcode
DC --> Translate (TR) [ gamble since who knows if the first instructions is a 32-bit word ]
It seems reasonable this code might start with a BALR:
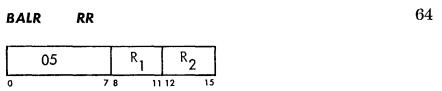
Can anyone determine if the above might be a valid S360 machine code sequence?
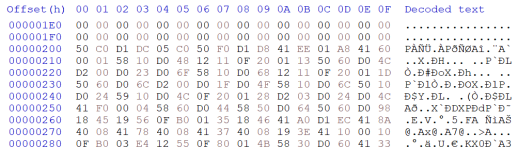
Here is another section:
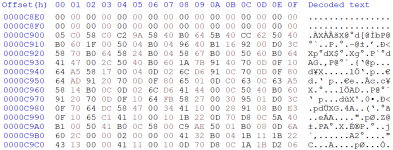
Then one more sample section: (I think the portion in the red box is data, an end of segment CRC since it falls right before the next segment of 0xA800)

But suppose the binary below (starting at 0x200) is some kind of S360 machine code. I don't think it is the earliest Model 20, don't think it is a Model 40. I do think some floating pointing code might be in there.
The arrangement is below is HxD on a Wintel platform. My understanding is the S360 was big-endian -- but I'm not exactly sure what that means. Meaning, do I reverse the entire byte? Or do I just swap bytes within a word?
For example, the sequence below starts with "50 C0 D1 DC" (I understand not all S360 opcodes were 32-bit, but just examining the first "word" as an exercise)
How would that get interpreted by a S360?
Code:
Swap the nibbles: "05 0C 1D CD" ?
Swap the bytes: "C0 50 DC D1" ?
Swap the entire sequence: "CD 1D 0C 05" ?
Or: "DC D1 C0 50"Or maybe no adjustment is needed, if this binary was extracted in the same order the machine interprets it as? Under that premise, then are any of those even valid opcodes?
50 --> don't think this is a valid S360 opcode
05 --> Branch and Link (BALR)
C0 --> don't think this is a valid S360 opcode
CD --> don't think this is a valid S360 opcode
DC --> Translate (TR) [ gamble since who knows if the first instructions is a 32-bit word ]

It seems reasonable this code might start with a BALR:

Can anyone determine if the above might be a valid S360 machine code sequence?
Here is another section:

Then one more sample section: (I think the portion in the red box is data, an end of segment CRC since it falls right before the next segment of 0xA800)